In recent months the UK’s data protection authority, the Information Commissioner’s Office (ICO), has begun publishing data sets naming organisations that have been subject to reprimands, complaints, and various other concerns brought to its attention. Many organisations had previously assumed that information would not be made public.
Equivalent data is not commonly published by EU data protection authorities and this development marks a significant regulatory change that has important implications for organisations regulated by the ICO.
Reprimands
If the ICO finds that an organisation has not complied with UK data protection law, it has various powers at its disposal, including the ability to:
- impose substantial fines;
- require corrective actions; and
- limit or ban data processing.
The ICO has a track-record of publishing details of fines, enforcement notices, undertakings and prosecutions on its website.
One of the softer tools in the ICO’s regulatory armoury is the reprimand: a letter stating that the ICO believes that an organisation has not complied with the law, which is often accompanied by a list of reasons for the decision and any recommended actions. Reprimands do not require organisations to pay a fine or take specific actions; rather, they are often used where the infringement is not serious enough to justify a fine or in line with the ICO’s revised approach to enforcement against public sector bodies.
While the ICO had previously stated that reprimands would not usually be published, in November 2022, the new head of the ICO, John Edwards, announced that the ICO would publish all reprimands going forward—including reprimands issued from January 2022 onwards.
The background to the change is the ICO’s revised approach to public sector enforcement, which attempts to reduce the impact of fines on public sector bodies. This means making much greater use of other tools, such as reprimands. It is therefore important that reprimands are made public to share good practice. However, the ICO has also decided that it would be unfair for only public sector reprimands to be published.
The ICO reserves the right not to publish a reprimand where there is a good reason. Examples of ‘good reasons’ provided by the ICO—relating to matters of national security, or where that it is likely to jeopardise any ongoing investigation—suggest that most reprimands will be published going forwards.
Complaints and concerns
In line with its commitment to being both open and transparent about its work, the ICO has also begun to publish new data sets on various ‘complaints and concerns’ brought to its attention in recent years.
The sets include information on:
- data protection and freedom of information complaints raised by members of the public;
- self-reported personal data breaches;
- civil investigations;
- cyber investigations;
- investigations under the UK’s ePrivacy regime; and
- investigations by the ICO’s Financial Recovery Unit.
The data sets are published in a reusable format, and include the names of the organisations concerned, the legislation involved, and the outcome of the ICO’s investigations. Importantly, the data sets include the names of the organisations investigated, even when no infringement has been found.
While those data sets provide far less detail than reprimands, they will still be the cause of some concern to organisations that are fearful of adverse publicity or attracting unwanted scrutiny.
The availability of these data sets is likely to be relevant in due diligence on transactions, particularly to get a feel for the level of risk and dispute frequency associated with a company’s privacy posture.
The data sets also provide some interesting insights into the ICO’s workload.
For example, in the period covered by the data most self-reported data breaches did not relate to cybersecurity events:
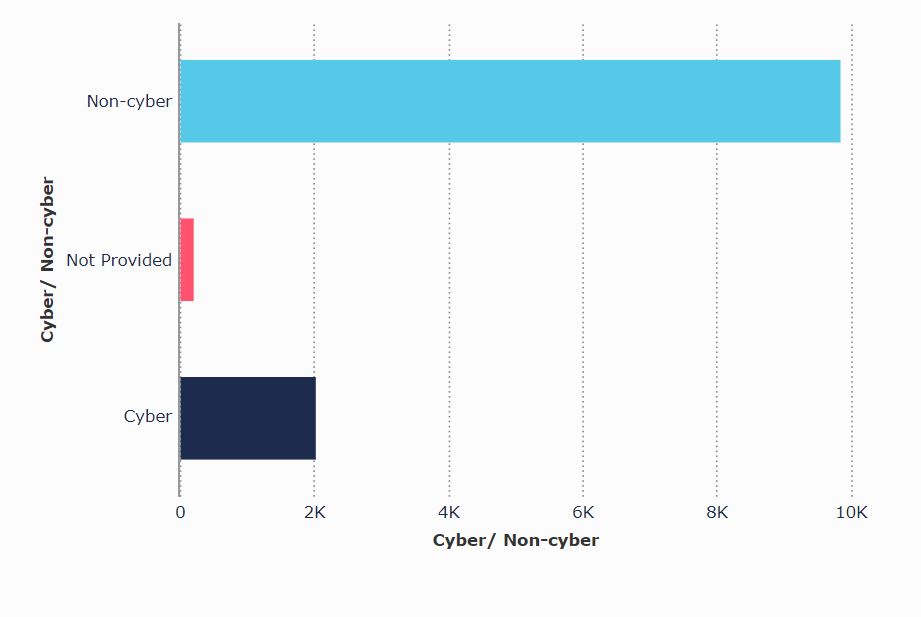
The data also shows that in the relevant period the health, education and childcare sectors were the most likely to self-report a data breach:

Implications
Publicity is often one of the key concerns of organisations following a data complaint or incident.
As such, the greater risk of breaches and other causes of concern being made public must be considered when planning data protection compliance, evaluating how to respond to a potential breach, and engaging with the ICO.
The detailed information made available in a reprimand sets it apart from the other data sets the ICO has published. Organisations faced with a potential reprimand are now more likely to wish to challenge it, to avoid being publicly chastised.
Unfortunately, organisations faced with reprimands lack a clear appeals mechanism once a reprimand has been imposed because reprimands are not listed as one of the ICO’s enforcement powers that can be appealed to the Information Tribunal. This underscores the importance of ensuring engagement with the ICO in relation to any potential infringement is carefully handled from the outset.
While the data on other ‘complaints and concerns’ is less detailed and has been released in a relatively understated way, organisations may also be concerned about that information being publicly available.
Organisations may be particularly concerned about how the reprimands and other new data may be used by groups such as:
- journalists;
- customers;
- privacy-advocates;
- advisors undertaking due diligence on a target company ahead of a potential acquisition;
- potential claimants; and
- law firms seeking to identify opportunities to bring group compensation claims.
Organisations are often required to make finely balanced judgements when deciding if a data breach should be notified to the ICO. Some organisations may now err less on the side of notification and report fewer data breaches.
The publication of those data sets and reprimands may also increase the leverage of data subjects, and place additional pressure on organisations to resolve disputes before the complainant notifies the ICO.
It is more important than ever for organisations that have suffered a data breach or face potential enforcement to work with advisors that are experienced in engaging with the ICO.


